When deploying virtual machines in Azure you have to think about alot of things. You are not finished with just a virtual machine. You need to have a way to backup, update, manage, monitor your virtual machines.
In this blogpost I’ll talk about installing Azure Extensions on your Azure Virtual Desktop session hosts to help you with these things. As always the code for this can be found on my Github.
Importing resources
Since the session host used in this example already exists, I’m using a data block to import it into this terraform file.
data "azurerm_virtual_machine" "avd-1" {
provider = azurerm.hub
name = "avd-prd-jvn-0"
resource_group_name = "rg-prd-jvn-avd-session-hosts-01"
}BGInfo
An extension that alot of people who have worked alot with on-premise servers like is BGInfo. This will put useful info about the virtual machine on the desktop.
To install this I’m using a Terraform “null_resource” and run the Azure CLI command to intall the extension on the virtual machine
resource "null_resource" "bginfo-avd-1" {
provisioner "local-exec" {
command = "az vm extension set --name BGInfo --publisher Microsoft.compute --resource-group rg-prd-jvn-avd-session-hosts-01 --vm-name avd-prd-jvn-0"
}
}Azure Monitoring agent
This agent is going to replace the older Microsoft Monitoring Agent. Installing the extension is only the first part. after the installation you need to link it with your Log Analytics workspace. This can be done using a Data Collection Rule and Azure Policy.

The Azure Monitoring agent can also be deployed using a null resource and the Azure CLI command.
Important to know is that the Azure Monitor Agent requires a managed identity on the virtual machine. This can be a user or system managed identity.

resource "null_resource" "AzureMonitoringAgent" {
provisioner "local-exec" {
command = "az vm extension set --name AzureMonitorWindowsAgent --publisher Microsoft.Azure.Monitor --ids ${data.azurerm_virtual_machine.avd-1.id} --enable-auto-upgrade true"
}
}Microsoft Monitoring Agent
Although this agent is gonna to be replaced by the Azure Monitoring Agent, you can still use it. For this extension I’m using the extension resource for Terraform. The Log Analytic workspace ID and key are passed in using variables.
resource "azurerm_virtual_machine_extension" "mmaagent" {
provider = azurerm.hub
name = "MicrosoftMonitoringAgent"
virtual_machine_id = data.azurerm_virtual_machine.avd-1.id
publisher = "Microsoft.EnterpriseCloud.Monitoring"
type = "MicrosoftMonitoringAgent"
type_handler_version = "1.0"
auto_upgrade_minor_version = true
settings = <<SETTINGS
{
"workspaceId": "${var.workspace_id}"
}
SETTINGS
protected_settings = <<PROTECTED_SETTINGS
{
"workspaceKey": "${var.workspace_key}"
}
PROTECTED_SETTINGS
}When you check the Log Analytics Workspace you can see that the session host is connected using both agents.
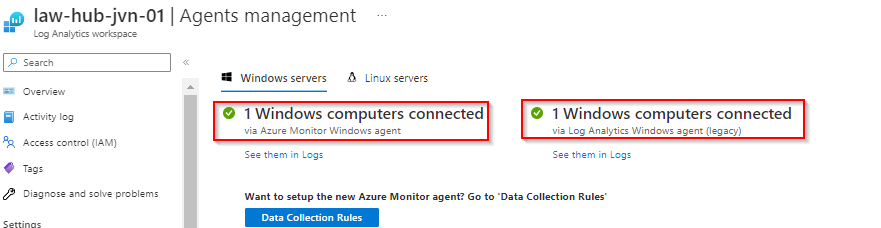
Dependency Agent
If you are still using the Log Analytics Agent, you also still need the dependency agent. The Dependency Agent collects data about processes running on the virtual machine and external process dependencies.
resource "azurerm_virtual_machine_extension" "da" {
provider = azurerm.hub
name = "DAExtension"
virtual_machine_id = data.azurerm_virtual_machine.avd-1.id
publisher = "Microsoft.Azure.Monitoring.DependencyAgent"
type = "DependencyAgentWindows"
type_handler_version = "9.5"
auto_upgrade_minor_version = true
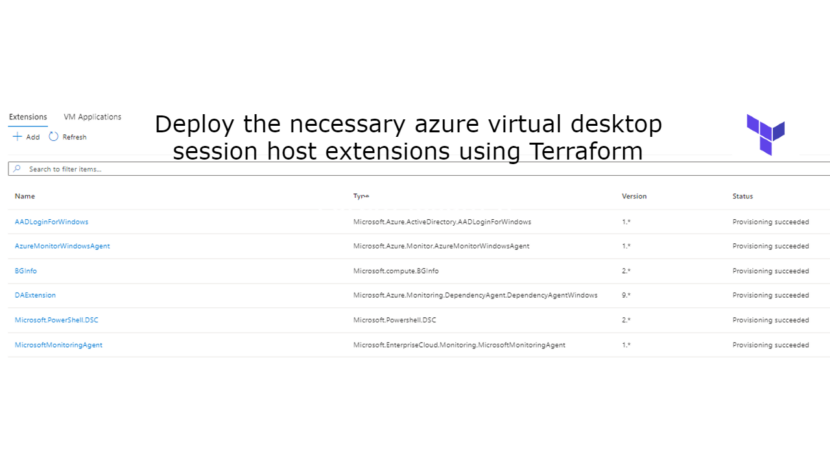
}After deployment you can check the installed extensions as you can see in the screenshot below.
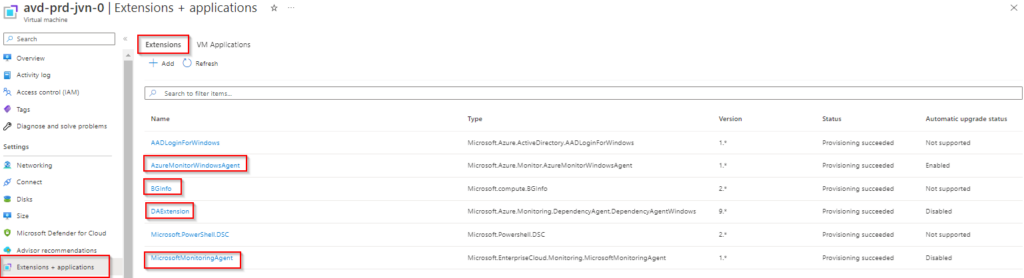
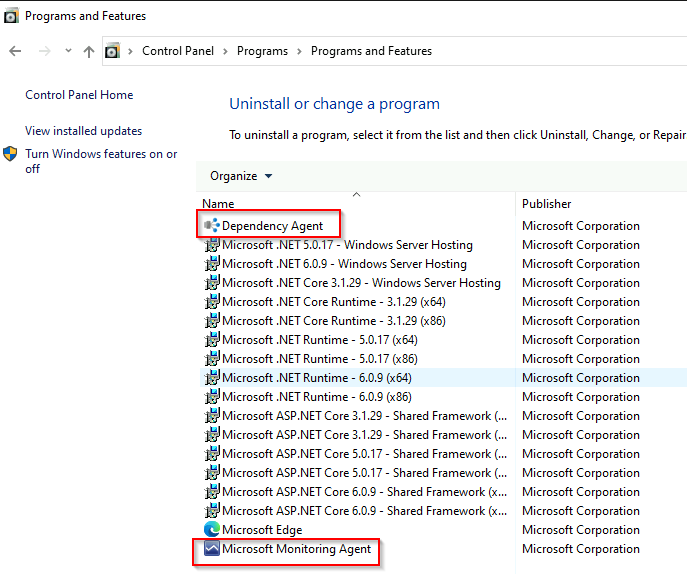
You can also see the Dependency agent and Microsoft Monitoring agent in the control panel.
The installed extensions are also visible on the virtual machine in the C:\Packages folder.
This concludes this blogpost about installing extensions on your avd session hosts. I hope this blogpost is useful for you. If you have any questions, feel free to contact me.