Hi there,
Welcome to another blog post about Azure and AVD in combination with Terraform. I while ago I showed you how to enable Azure Disk Encryption on your AVD session hosts using a scripted action in Nerdio. You can read that blog here.
I used a existing key vault in that blog and in this blog I’ll show you how to deploy the Key Vault.
In this blog post I’m focussing on the key vault itself. I’m not going to harden the key vault, this will be for another blog post.
First of al we need a couple of resources deployed before we can start:
- management resource group for key vault
- Low Analytics Workspace for diagnostic settings
data "azurerm_resource_group" "rg-kv" {
provider = azurerm.hub
name = "rg-${var.env}-${var.prefix}-${var.solution}-management-01"
}
data "azurerm_log_analytics_workspace" "law" {
provider = azurerm.hub
name = "law-hub-${var.prefix}-01"
resource_group_name = "rg-hub-${var.prefix}-management-01"
}
Now let’s have a look at the code for an key vault. For the Azure Disk Encryption to work it’s important to put enabled_for_disk_encryption on true.
resource "azurerm_key_vault" "kv" {
provider = azurerm.hub
depends_on = [ data.azurerm_resource_group.rg-kv ]
name = "kv-${var.env}-${var.prefix}-${var.solution}-96"
location = data.azurerm_resource_group.rg-kv.location
resource_group_name = data.azurerm_resource_group.rg-kv.name
tenant_id = data.azurerm_client_config.current.tenant_id
soft_delete_retention_days = 7
purge_protection_enabled = false #be careful with this feature
enabled_for_deployment = true
enabled_for_template_deployment = true
enabled_for_disk_encryption = true
public_network_access_enabled = false
sku_name = "standard"
tags = {
"Costcenter" = "IT"
"Critical" = "Yes"
"Environment" = "prd"
"Solution" = "Keyvault"
}
}
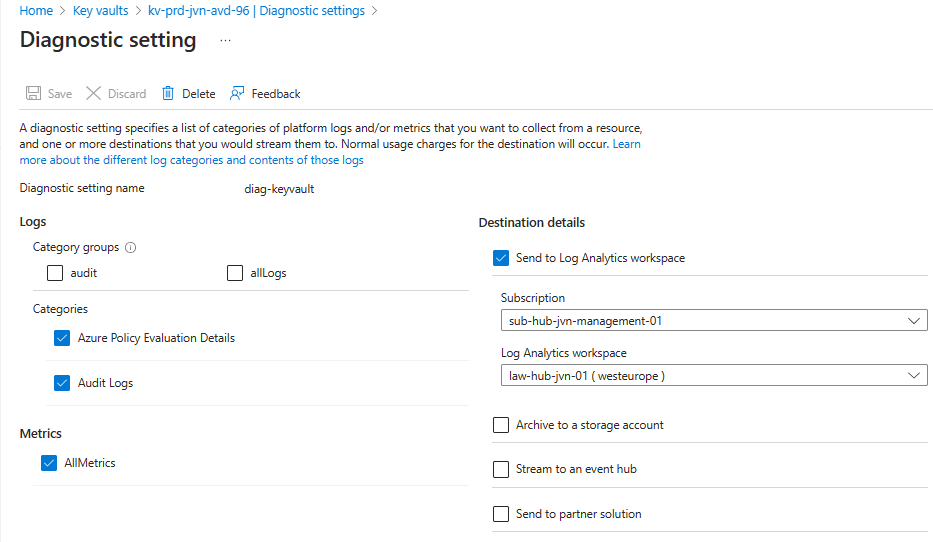
resource "azurerm_monitor_diagnostic_setting" "kv-diag" {
name = "diag-keyvault"
target_resource_id = azurerm_key_vault.kv.id
log_analytics_workspace_id = data.azurerm_log_analytics_workspace.law.id
log {
category = "AuditEvent"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "AzurePolicyEvaluationDetails"
enabled = true
retention_policy {
enabled = true
}
}
metric {
category = "AllMetrics"
retention_policy {
enabled = true
}
}
}
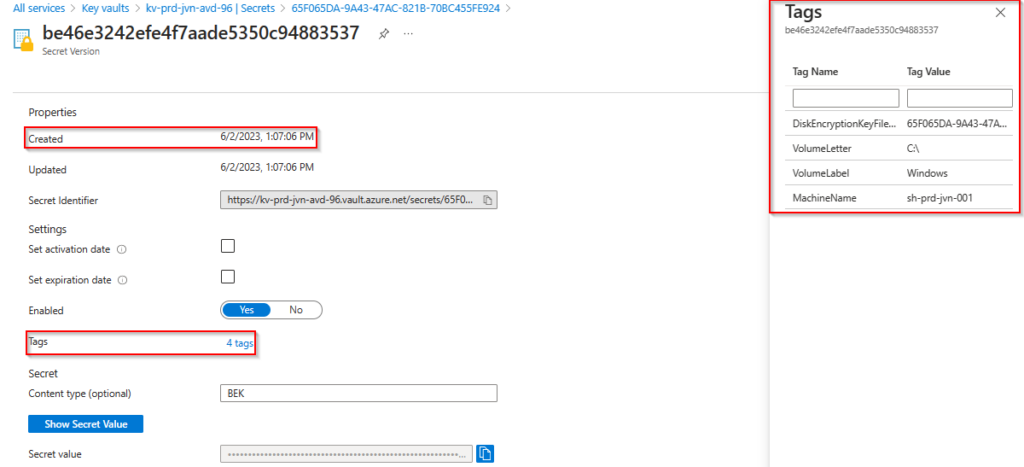
In my previous blogpost I showed you how you can use a Nerdio Scripted Action to encrypt a session host’s OS disk. When the activation of Bitlocker is done we can find the secrets in the key vault.
Note that when you re-image the session hosts and you enable ADE on the host that you will get a new secret. You can this below see 10 secrets that I got from re-imaging 2 session hosts.
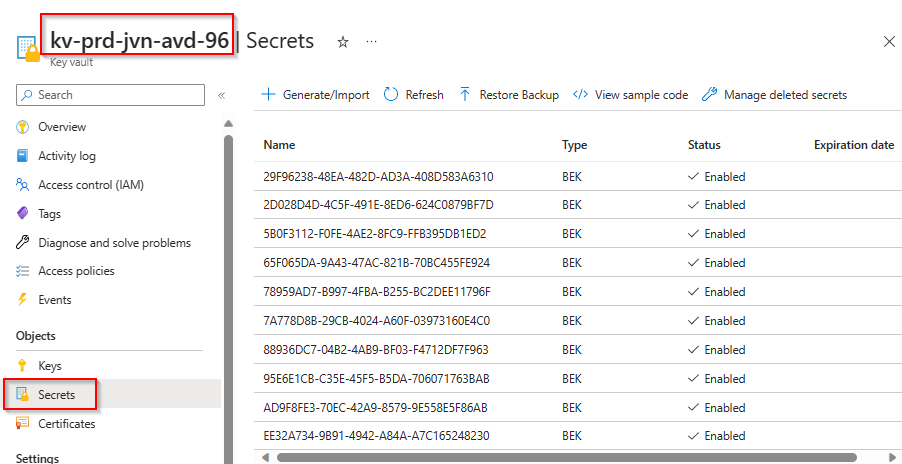
Where to find the secret?
Now that we have the bitlocker active on the session hosts it’s time to check the secrets in the key vault. When you select the secret and select the tags you can see for which host it is, the volume label and when the secret was created.
There we go, I hope this blog post will help you to setup a key vault for ADE. In case you have any questions, feel free to contact me.
1 thought on “Deploy an ADE enabled Key Vault for AVD with Terraform”