Hi All,
Welcome in this 3rd part of my Harden Nerdio Manager for Enterprise blog series. In this blog series I take a look at the security of the Nerdio Manager for Enterprise. In the previous posts I looked at the App Service and SQL. In case you missed those posts you can read them through the links. In this part I’m going to focus on the storage accounts of Nerdio.
These days security should be a big point of attention for each company. You should try to limit the access to each service. In case of the storage account we are going to limit the level of access.
We only want to allow the Nerdio app service access to the storage accounts. We can achieve this by using the vnet integration subnet from the app service. This makes sure that only the outbound traffic of the app service has access to the storage account.
To achieve this we need to open the networking blade of the storage account, and add the app service subnet to the virtual networks.

As you can read in the blog post about hardening the App Service, I created an extra subnet for the outbound traffic. We will add this to the storage account.

You get the message first that the service endpoint for storage needs to be enabled first.
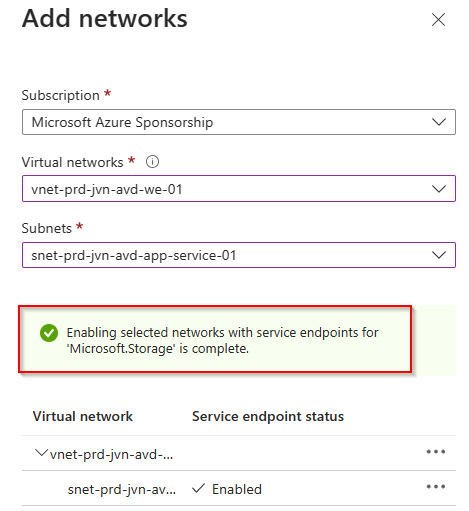
When the config is done don’t forget to click on save.

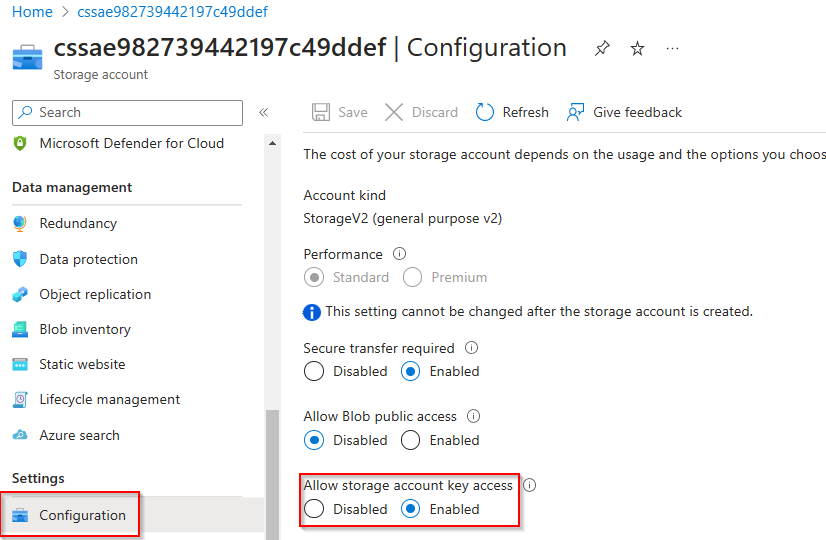
Another way of adding more security to the storage accounts is to deny the ability to connect to the storage account with account keys? This is by default enabled but you can disable this. Disabling the account keys will also disabled the ability of using a SAS (Shared access Signature).
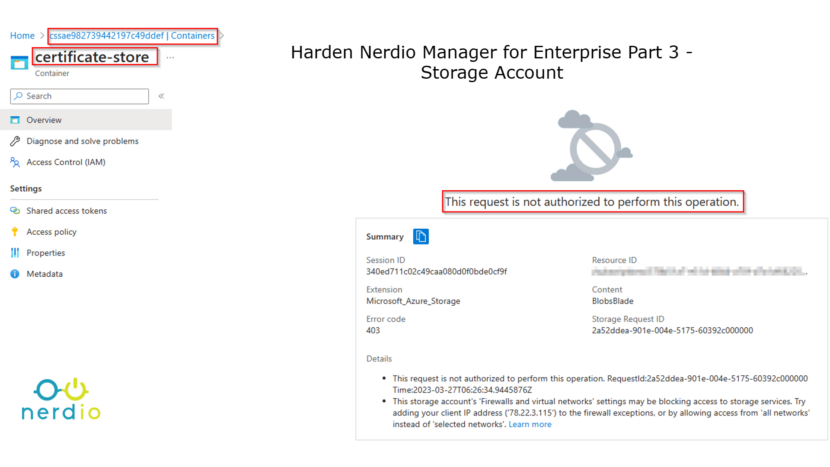
With the network hardening in place, I go the Certificate store container in the storage account from my laptop and I get the following message. Only the Nerdio App Service is now able to access the storage account through the subnet.
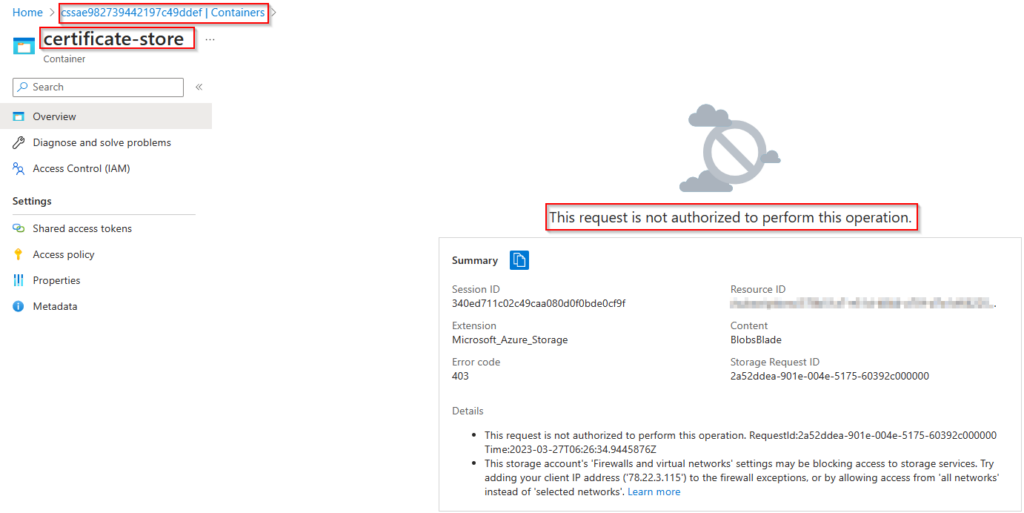
I only showed the process with 1 of the 3 Nerdio’s storage accounts but you can do this with all 3 of them.
This concludes part 3 of this series, stay tuned for part 4 where I’ll cover the Nerdio keyvault.