The last couple of years we had to rely on ADDS or AADDS for the FSLogix permissions. Last year Microsoft introduced a new way of authenticating.
Azure AD Kerberos was introduced last year as a third option. This is a a great solution for customers who want to go cloud only. If you want to learn more about Azure AD Kerberos works, check out this link.
Also important that you still need to use Hybrid identities in order to make this work. You can however use the following workaround from Marcel Meurer. This way you can use Cloud only accounts. You can view his workaround here.
In this blog post I’m going to focus on configuring Azure AD Kerberos on the storage accounts that we are going to use for the FSLogix profiles. You can do this through the Azure portal but I’ll show you how you can automate this with Terraform.
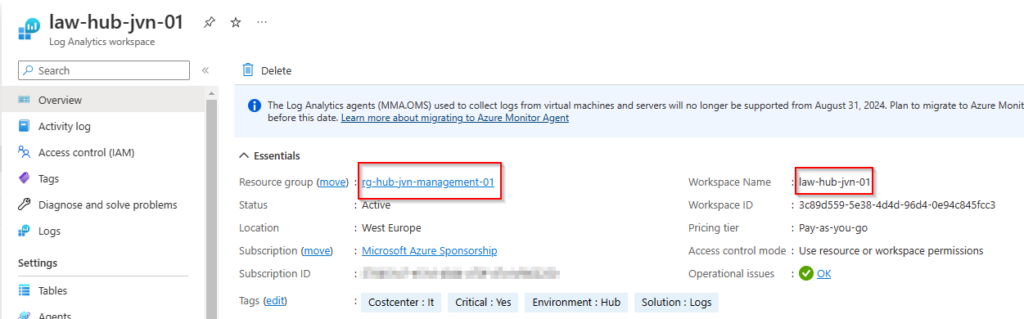
The first resource that we need is the Log Analytics workspace for the diagnostic settings of the storage account and the file share.
data "azurerm_log_analytics_workspace" "law" {
provider = azurerm.hub
name = "law-${var.hub}-${var.prefix}-01"
resource_group_name = "rg-${var.hub}-${var.prefix}-management-01"
}
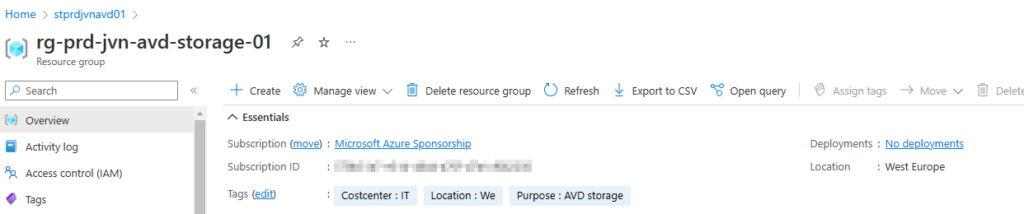
I deploy the resource group for my AVD storage in a different script. This means I have to use a data resource to import it.
data "azurerm_resource_group" "avd-rg" {
provider = azurerm.hub
name = "rg-${var.env}-${var.prefix}-${var.solution}-storage-01"
}
The next part is the storage account. There are some security aspects to consider here.
- Use private endpoints
- Don’t allow public access
- Enable https traffic only
- Use TLS version 1.2
resource "azurerm_storage_account" "avd-sa" {
provider = azurerm.hub
name = "st${var.env}${var.prefix}${var.solution}01"
resource_group_name = data.azurerm_resource_group.avd-rg.name
location = data.azurerm_resource_group.avd-rg.location
account_tier = "Premium"
account_replication_type = "ZRS"
account_kind = "FileStorage"
enable_https_traffic_only = true
allow_nested_items_to_be_public = false
#allow_blob_public_access = false
shared_access_key_enabled = false
public_network_access_enabled = false
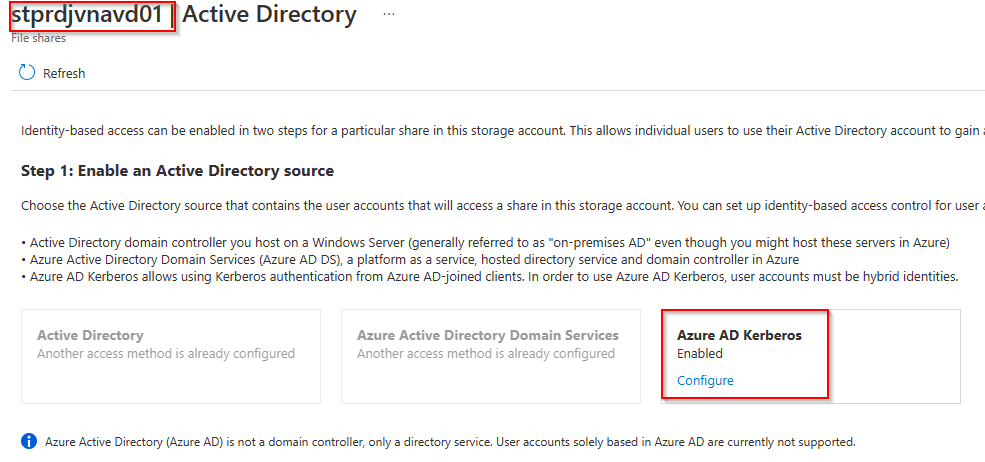
min_tls_version = "1.2"The option to configure the storage account with AAD Kerberos was released recently. You can enable it by adding the following lines of codes.
azure_files_authentication {
directory_type = "AADKERB"
}
Of course don’t forget to put the tags on the storage account. In this case I put the region in a tag and the storage redundancy.
tags = {
"location" = "westeurope"
"environment" = "prd"
"StorageTier" = "ZRS"
}Off course we also need a file share. To create it I use the following code.
resource "azurerm_storage_share" "fslogix" {
provider = azurerm.hub
name = "fslogix"
storage_account_name = azurerm_storage_account.avd-sa.name
depends_on = [azurerm_storage_account.avd-sa]
quota = "100"
metadata = {
"costcenter" = "iT"
"solution" = "Fslogix"
"environment" = "prd"
"critical" = "yes"
}
}Very important is the option to check the logs if needed if something is going wrong. For this we configure diagnostic settings that we send to the Log Analytics Workspace.
You can configure these on the storage account but also on the file share.
resource "azurerm_monitor_diagnostic_setting" "st-avd-diag" {
name = "diag-st-${var.solution}-jvn"
target_resource_id = azurerm_storage_account.avd-sa.id
log_analytics_workspace_id = data.azurerm_log_analytics_workspace.law.id
depends_on = [
azurerm_storage_share.fslogix
]
metric {
category = "Transaction"
retention_policy {
enabled = true
}
}
}
resource "azurerm_monitor_diagnostic_setting" "st-avd-diag-file" {
name = "diag-st-${var.solution}-jvn"
target_resource_id = "${azurerm_storage_account.avd-sa.id}/fileservices/default"
log_analytics_workspace_id = data.azurerm_log_analytics_workspace.law.id
depends_on = [
azurerm_storage_share.fslogix
]
enabled_log {
category = "StorageRead"
retention_policy {
enabled = true
}
}
enabled_log {
category = "StorageWrite"
retention_policy {
enabled = true
}
}
enabled_log {
category = "StorageDelete"
retention_policy {
enabled = true
}
}
metric {
category = "Transaction"
retention_policy {
enabled = true
}
}
}In the portal you’ll see the following.
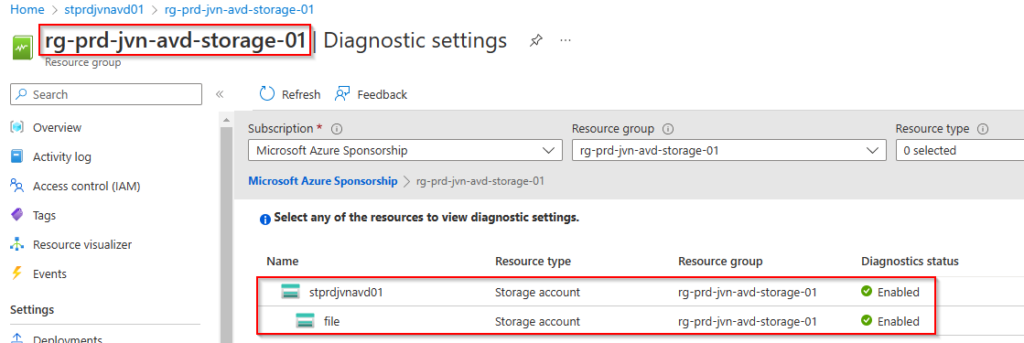
The final step we need to do to ensure that Azure AD authentication can work is to grant consent to the app registration that was created when we activated AAD Kerberos. Go to Azure AD > App Registrations > app registration from the storage account > API Permissions and grant consent.
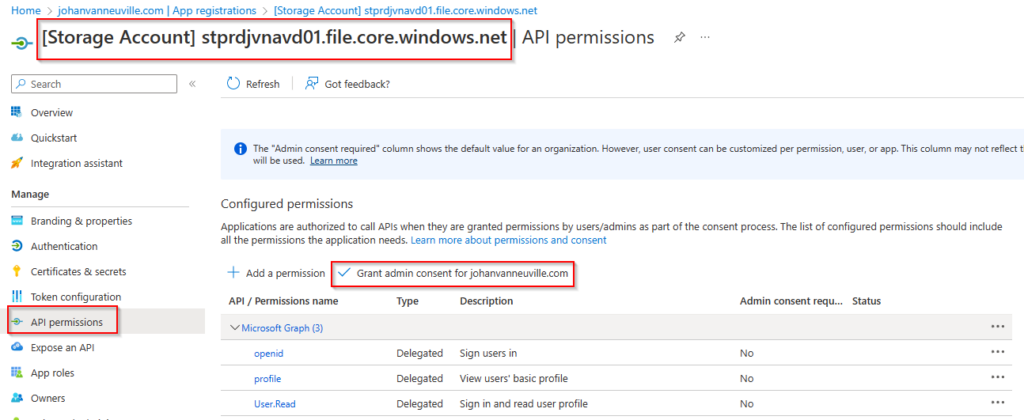
Now you only need to assign permissions to your users or groups that need access to the FSLogix share.
The full script can be found on my Github.
I hope this blog post will help you setup Azure AD Kerberos for your FSLogix file shares. In case you have any questions feel free to contact me.
1 thought on “Configure Azure AD Kerberos on an Azure File Share with Terraform”