
One of the requirements for Azure Virtual Desktop is storage. In this blog I’ll test AVD with Azure Files combined with Azure Private Endpoint, and look at the benefits from using this security feature.
Lets start with creating all the components that we need:
- storage account and FSLogix fileshare joined to my ADDS domain in West Europe
- hostpool and full desktop in West Europe
- Spoke vnet in West Europe with subnet for avd

One thing I want to avoid is public access on that storage account. In this setup it’s enough to provide the proper credentials from any network and Access is granted.
To avoid this I want to limit access with a Azure Private Endpoint. When doing this I can limit access for example an AVD sessionhost in the same vnet to the FSLogix File share.
Steps needed to configure Azure Private Endpoint
- create Private Endpoint
- Create DNS zone in Windows Domain for Private Endpoint
- Create dedicated subnet for private endpoint
Create Private Endpoint
Go to your Storage Account > Networking > Private Endpoint Connections tab and click on the + private endpoint button
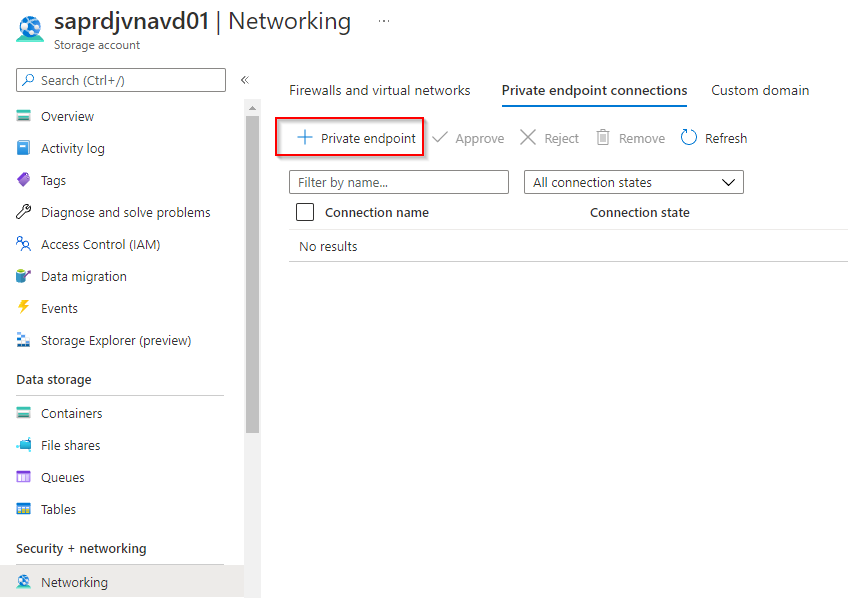
First tab is to choose the resource group en the name of the endpoint
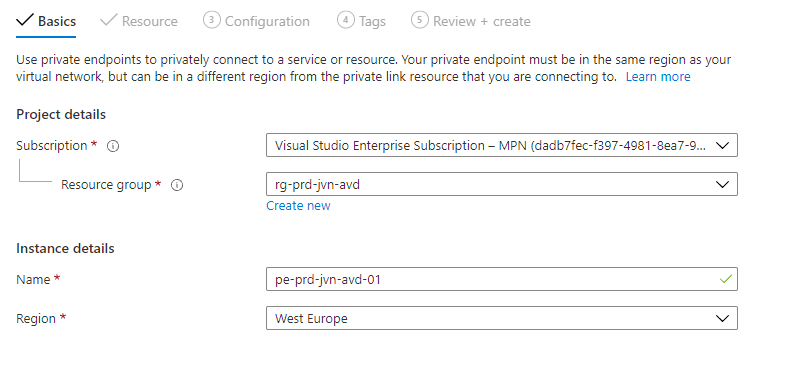
On the next tab we need to choose the resource we want to connect to the endpoint. Because I want to use the fileshare for FSLogix I’ll choose the file sub resource.
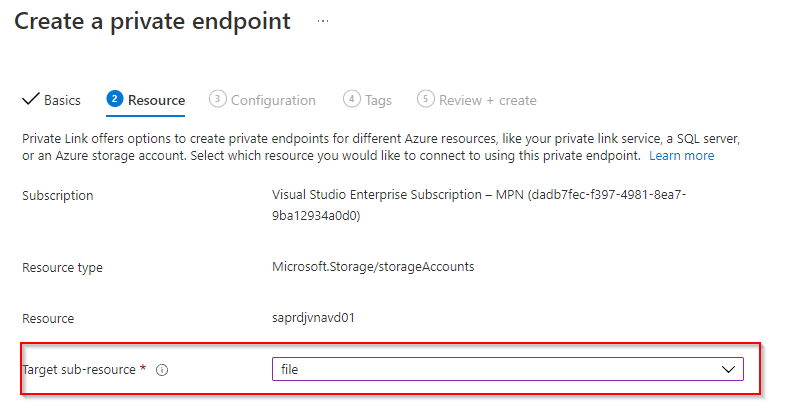
In the next screen you need to select you vnet and subnet. One thing you need to know is that your NSG that is connected with that subnet will be disabled.
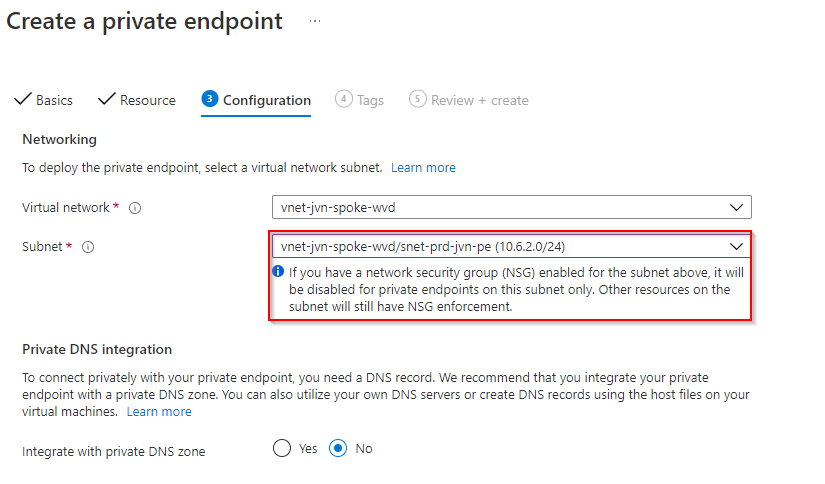
Also important is the option to integrate the endpoint with your private dns zone. I will create a private dns zone on my own domain
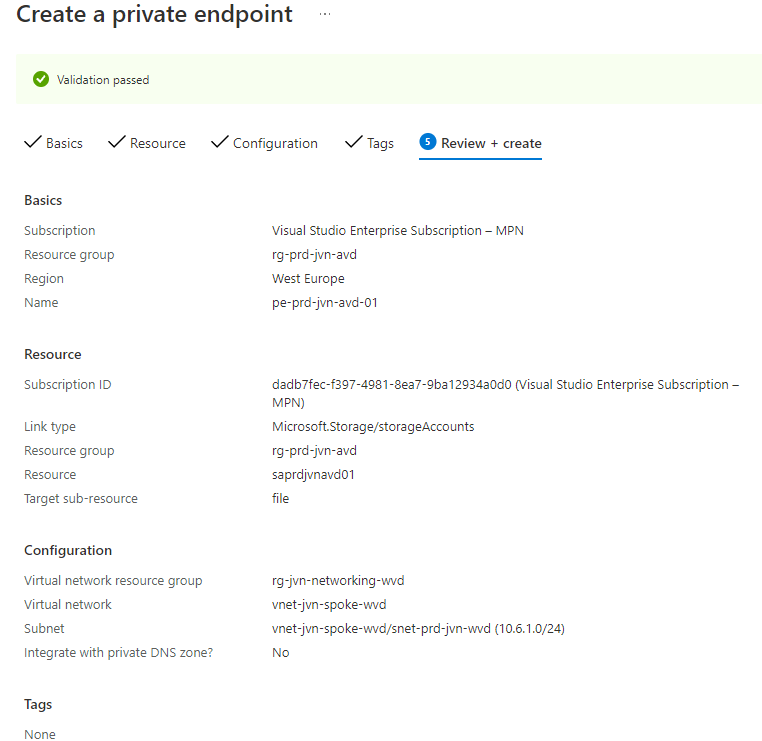
After the deployment we can see the endpoint on the Networking blade of the storage account
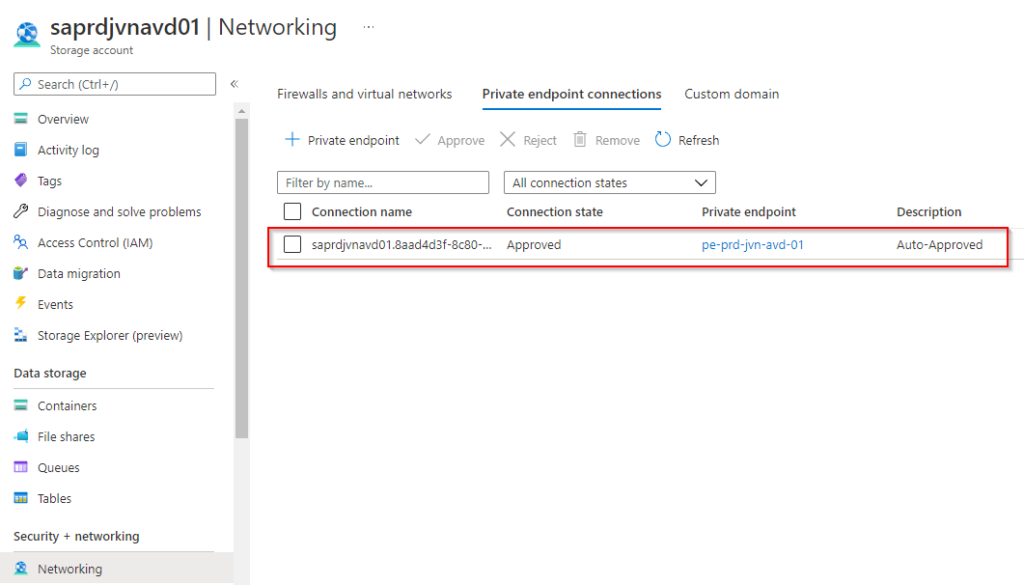
Create DNS zone in Windows Domain for Private Endpoint
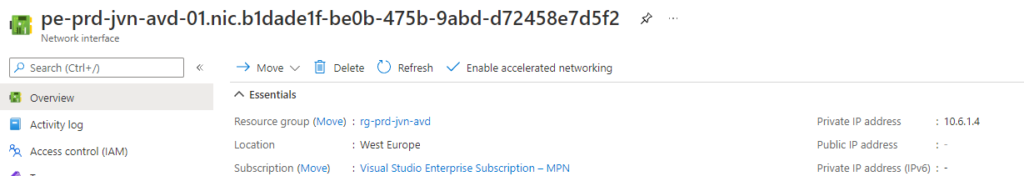
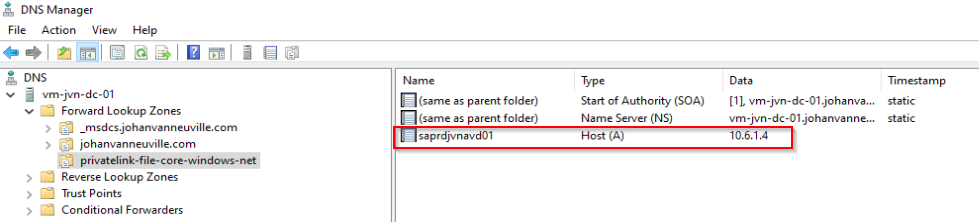
First I’ll check the ip adress of the endpoint because I need to this to create the DNS record on my domain controller.
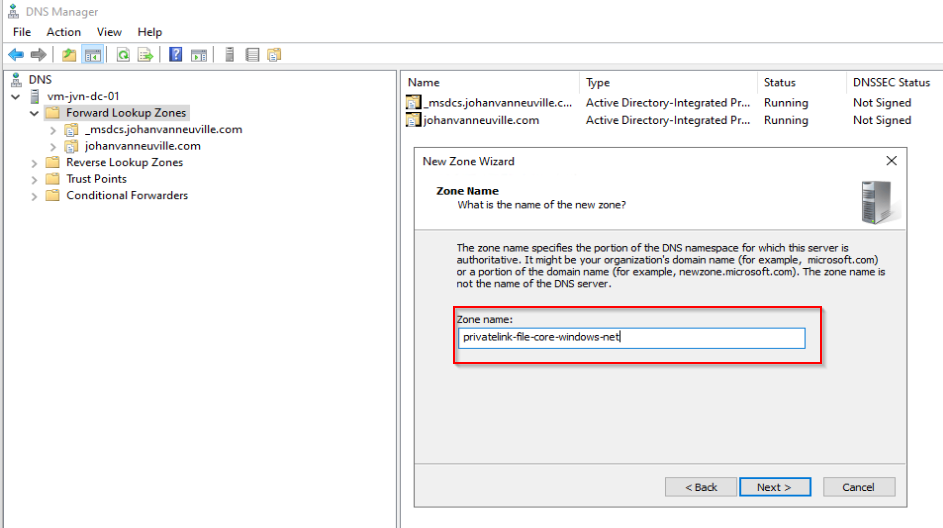
On my domain controller I open DNS and create a new Primary zone
After the zone is created I add an A record for the private endpoint
Benefits of using private endpoint
With this in place we can limit access to the storage account. Only session hosts that are in the same vnet as the private endpoint will be able to access the storage. When you have multiple regions for avd this is very usefull.