Hello and welcome to another blogpost about AVD in combination with Terraform. In this blogpost I’m gonna deploy an Azure Firewall with Terraform and apply the networking rules for AVD.
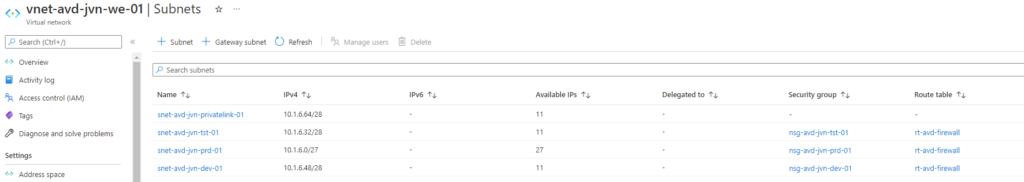
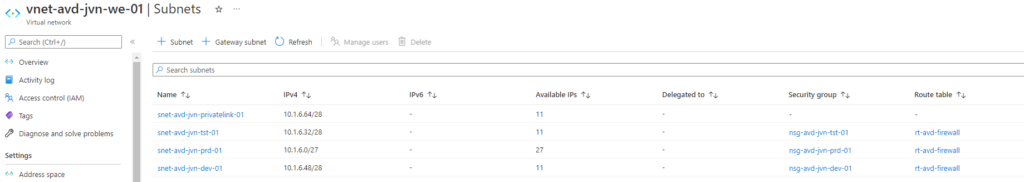
First of all we need a vnet for the AVD session hosts. I prefer to create a vnet for AVD and create multiple subnets per environment. (prd,tst,dev,..). This way I can easily create policies for the different AVD environments.
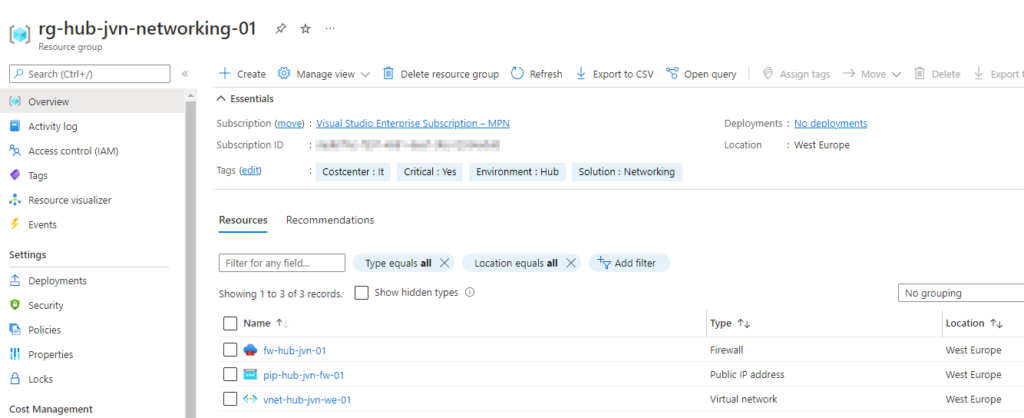
Now it’s time to deploy the firewall. In this case I’m using the standard version since it’s only for testing. For more info about Azure Firewall visit the doc’s page.
I’m deploying the firewall in my Hub Vnet and put the firewall in my hub networking resource group. The code is on my Github.
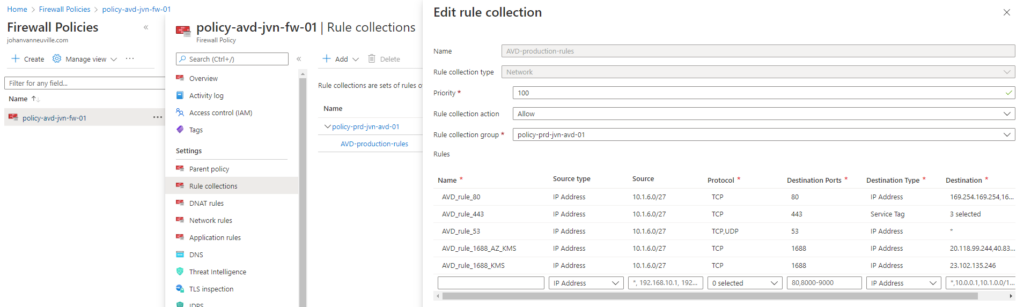
Below is the policy for the AVD subnet’s. This is created using a separate Terraform script. You can find this also on my Github. You can create separate policies per subnet if you change the source in the rule. The details on what rules you need to create can be found on the doc’s page
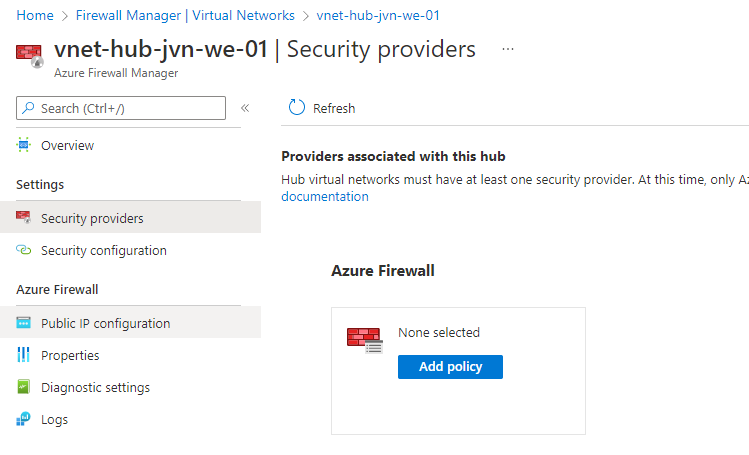
Now I need to assign the policy.
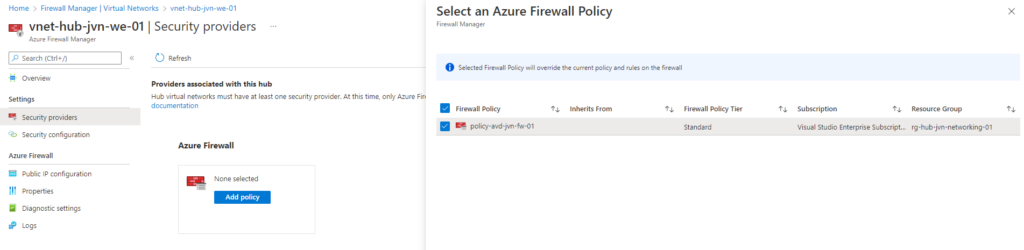
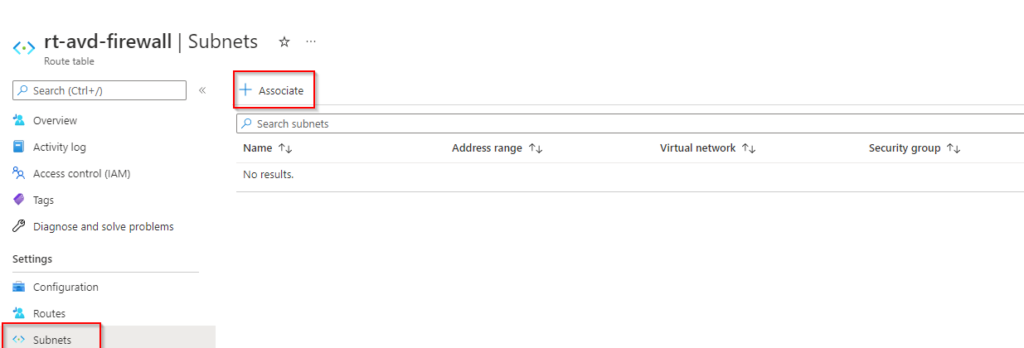
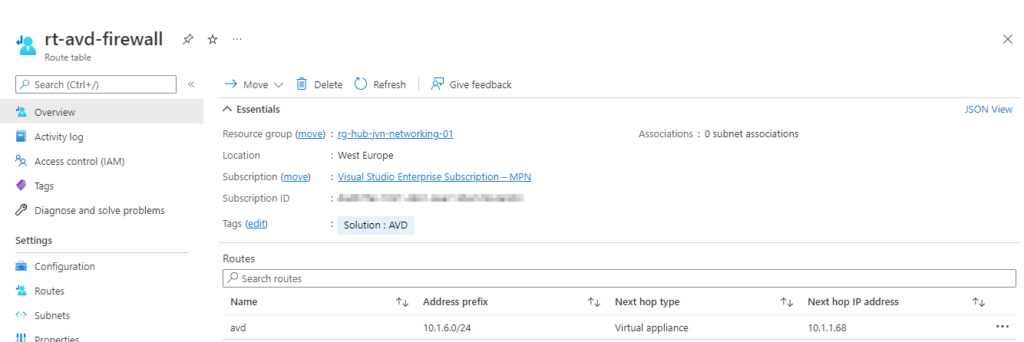
Besides the firewall policy I also create a route table and associate it with all 3 AVD subnets. In this route table I say that the next hop for all traffic from the 3 avd subnet’s is the private ip of the Azure Firewall. You can find this also on my Github
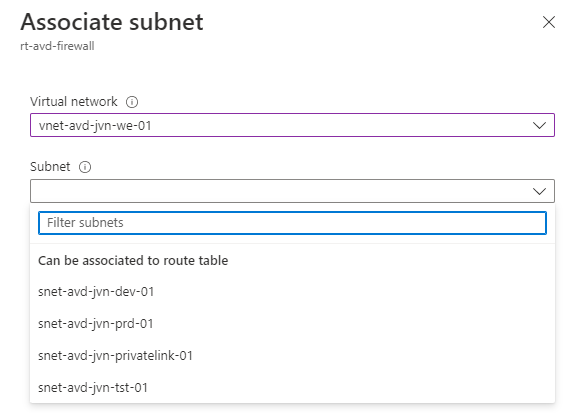
Choose all 3 subnet’s that I created in my AVD vnet.
This concludes my blog post about deploying Azure Firewall and AVD rules with Terraform. If you have any questions about this, feel free to contact me.
