Hello,
I’m back with another blogpost about Azure Virtual Desktop and Terraform. Since security is very important, I’m going to focus on that topic in this post. A very easy way to add more security to your AVD environment is to enable MFA for the users. Using MFA we can ensure that the users need an extra token to login. This can be an authenticator app, Fido key, answering a phone call or enter a code that you get by sms.
In this post I’m going to configure MFA for the AVD client app using conditional access.
Prerequisites
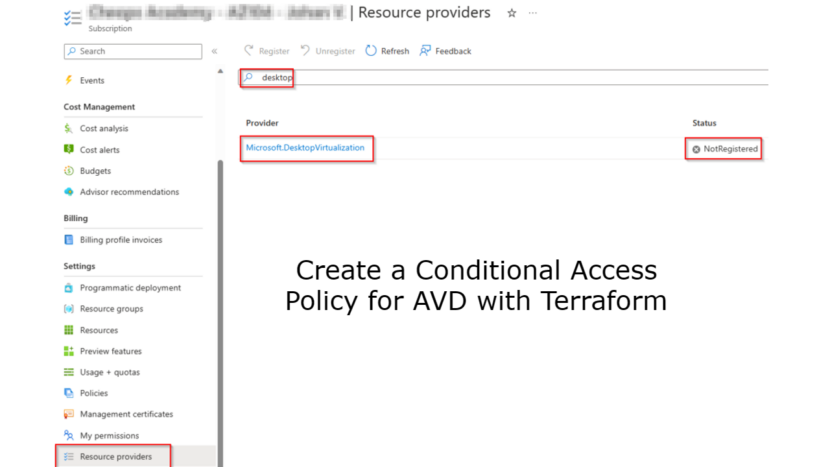
- You need to register the AVD provider on your subscription
- Have an Entra ID group to use in the cap to assign users
- Exclude your Break Glass accounts ideally with a security group
Register provider
The first thing you need to do is to register the DesktopVirtualization provider. Go to your subscription > resource providers > type in desktop. Select Microsoft.DesktopVirtualization and select register.
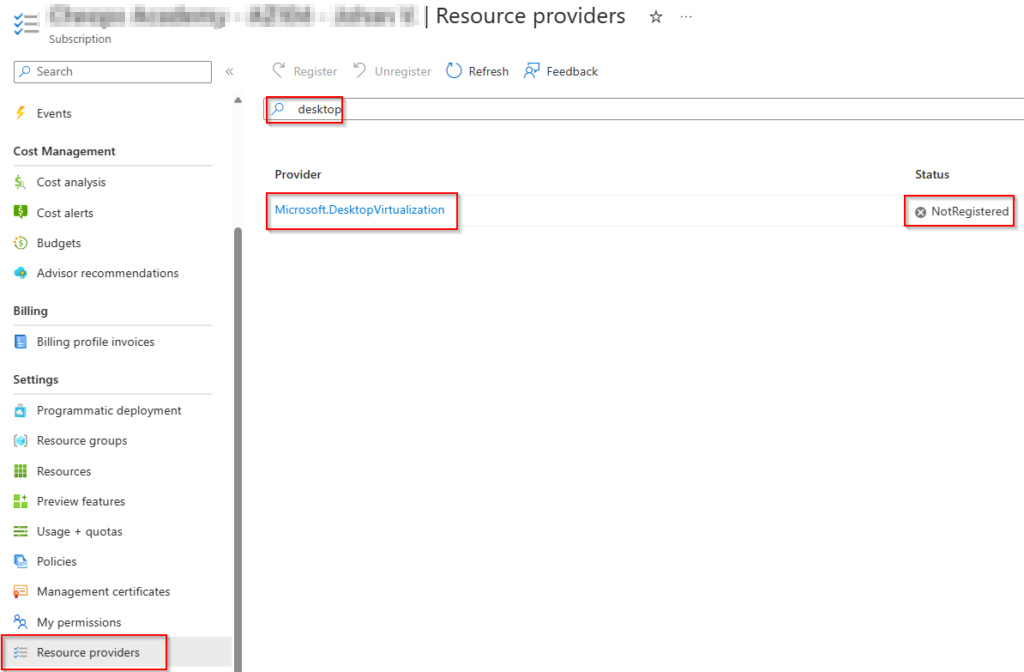
You will see the status change to Registering.
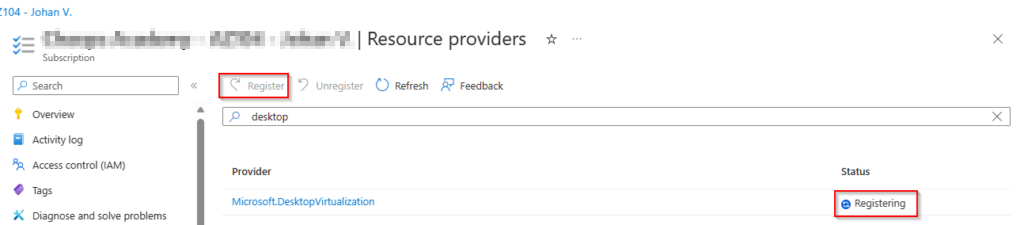
After a short time you will see the status coming to Registered.
Now it’s time for the Conditional Access policy. Important to know is that you need at least a Microsoft Entra ID P1 licence.
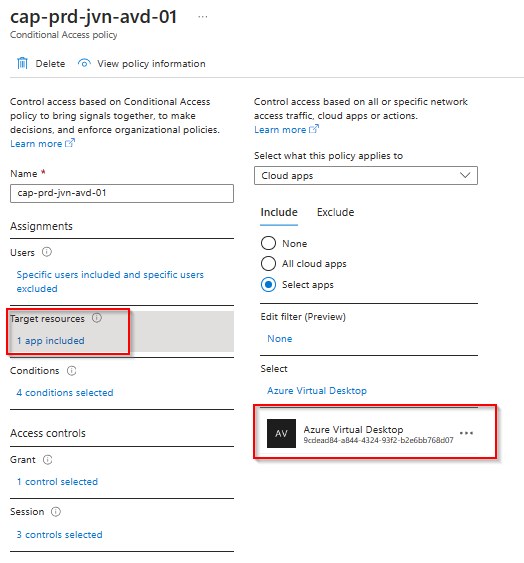
There are some important things in the cap policy.
- The application id for included applications
- The id of the Entra ID security groups
- Sign in frequency 4 hours in this example
- Applied to Windows platform
Important to know is that there are 2 different applications for AVD. If you registered the provider before the name change from WVD to AVD you will still see the Windows Virtual Desktop application.
terraform {
required_providers {
azuread = {
source = "hashicorp/azuread"
version = "~> 2.43.0"
}
}
}
data "azuread_client_config" "current" {}
provider "azurerm" {
features {}
alias = "hub"
subscription_id = var.subscription_id_mgmt
}
provider "azurerm" {
features {}
alias = "prod"
subscription_id = var.subscription_id_prd
}
provider "azurerm" {
features {}
alias = "identity"
subscription_id = var.subscription_id_identity
}
provider "azurerm" {
features {}
alias = "avd"
subscription_id = var.subscription_id_avd
}
resource "azuread_conditional_access_policy" "avd-prd" {
display_name = "cap-prd-jvn-avd-01"
state = "enabled"
conditions {
client_app_types = ["all"]
sign_in_risk_levels = ["medium"]
user_risk_levels = ["medium"]
applications {
included_applications = ["9cdead84-a844-4324-93f2-b2e6bb768d07"]
excluded_applications = []
}
locations {
included_locations = ["All"]
excluded_locations = ["AllTrusted"]
}
platforms {
included_platforms = ["windows"]
excluded_platforms = ["iOS","android","linux","windowsPhone"]
}
users {
included_groups = ["fb6e289a-465f-4434-bb3b-968ee737e6ab"]
excluded_groups = ["d6c3e0e4-8991-4f75-b179-978c00d11437"]
}
}
grant_controls {
operator = "OR"
built_in_controls = ["mfa"]
}
session_controls {
application_enforced_restrictions_enabled = true
sign_in_frequency = 4
sign_in_frequency_period = "hours"
cloud_app_security_policy = "monitorOnly"
}
}When the policy is deployed we can check the details.
The included security group

We can also check the excluded groups. In this case the group that includes the break glass accounts.
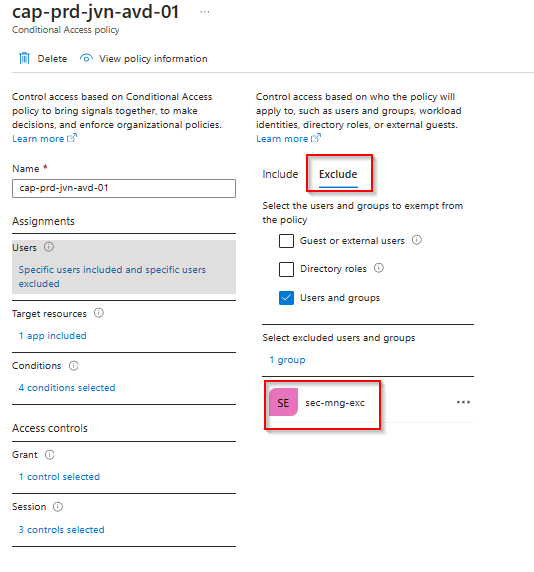
In the target resources we can see the AVD or WVD application depending on the resource provider.
With this policy in place, all the users in that security group will be prompted to use their MFA the next time they want to use the remote app for AVD.
I hope this blog post will help you to configure MFA through conditional access if you haven’t done this already.
1 thought on “Create a Conditional Access Policy for AVD with Terraform”