Hello everybody,
Welcome to another blogpost about Azure Virtual Desktop. In this blog post I’m going to talk about security. One of the first things to do when you create a new subscription for AVD is to enable the Defender for Cloud plans.
Defender for Cloud is a cloud-native application protection platform (CNAPP) that will help you keeping your environment safe. You can start using Defender for Cloud in the free tier. In this blog post I’ll show you how to enable the Standard Defender for Cloud plans Standard tier. For more info about Defender for Cloud, check out this link.
Prerequisites
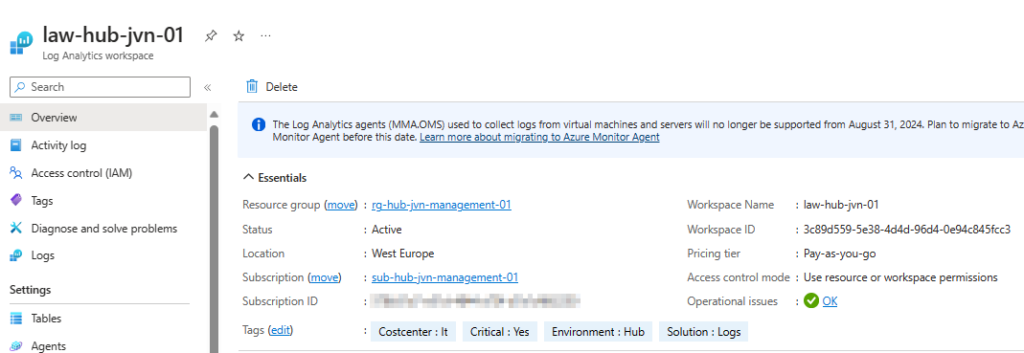
One of the settings of the Defender plans it to configure a custom Log Analytics Workspace for the Servers plan.
data "azurerm_log_analytics_workspace" "law" {
provider = azurerm.hub
name = "law-${var.env}-${var.prefix}-01"
resource_group_name = "rg-${var.env}-${var.prefix}-management-01"
}
Since you need to enable Defender per subscription you need to select the correct subscription. You can use the following line of code.
az account set --subscription "Your subscription id"Since some settings for Defender are not available in the Terraform Azurerm provider, we need to add 2 providers in the Terraform file. We need the Azurerm and Azapi provider.
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "=3.43.0"
}
azapi = {
source = "azure/azapi"
version = "=0.3.0"
}
}
}Email notifications
One of the settings that we can configure for Defender is the notifications that can be done through mail. You can specify a email and phone number.
resource "azurerm_security_center_contact" "sec-contact" {
email = ""
phone = ""
alert_notifications = true
alerts_to_admins = true
}
Activate Defender plans
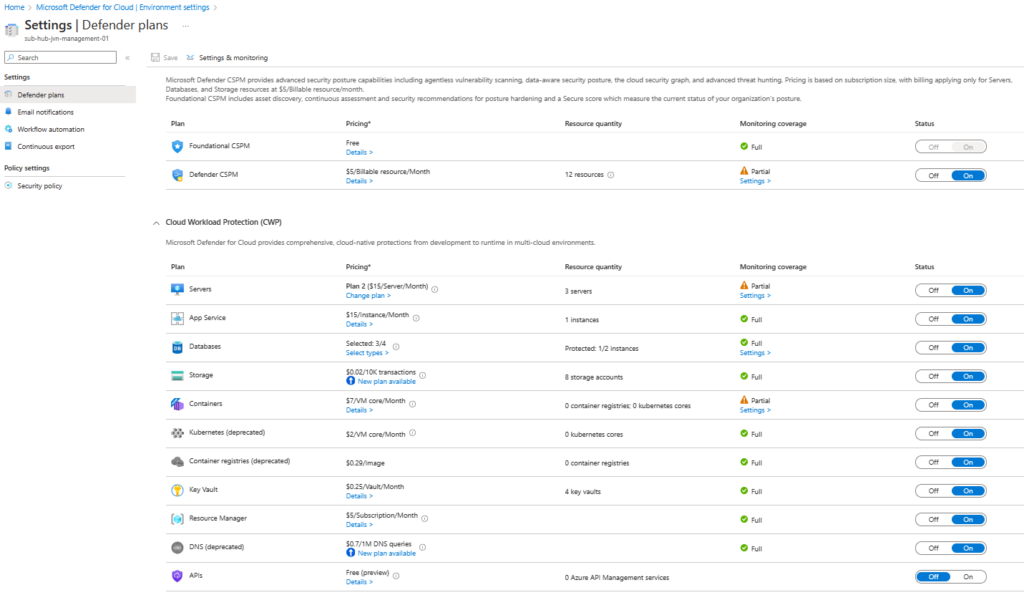
To make it easy to activate certain Defender plans, I have put them all into a Terraform local.
locals {
defender_plan = toset([
"VirtualMachines",
"KeyVaults",
"AppServices",
"SqlServers",
"OpenSourceRelationalDatabases",
"SqlServerVirtualMachines",
"StorageAccounts",
"KubernetesService",
"Dns",
"Arm",
"ContainerRegistry",
"CloudPosture",
"Containers",
])
}To activate the Defender plans I create the following resource.
resource "azurerm_security_center_subscription_pricing" "sc-hub" {
provider = azurerm.hub
for_each = local.defender_plan
tier = "Standard"
resource_type = each.key
}
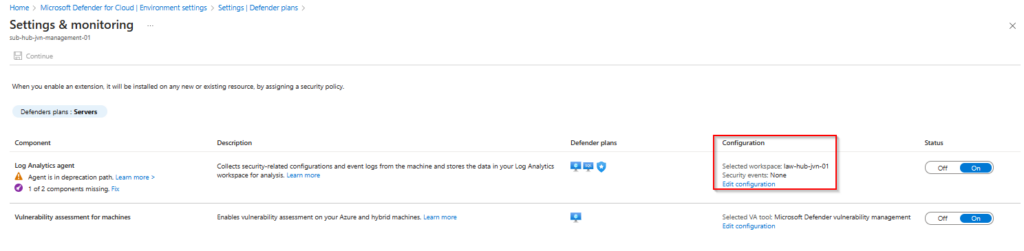
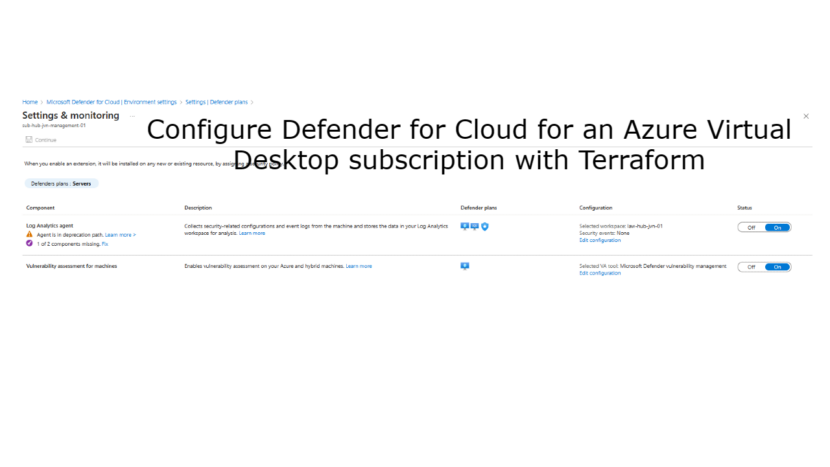
When we select the Servers plan Monitoring Coverage we can see the custom config. This config is done with the following code.
resource "azurerm_security_center_auto_provisioning" "autop" {
auto_provision = "On"
}
resource "azurerm_security_center_workspace" "law" {
scope = data.azurerm_subscription.current.id
workspace_id = data.azurerm_log_analytics_workspace.law.id
}
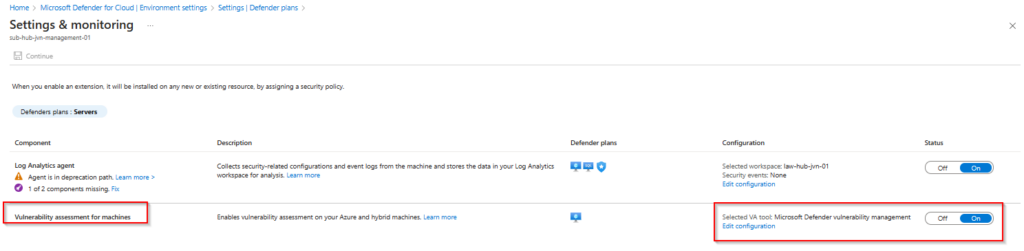
The Vulnerability assessment for machines is configured with the following Terraform code. For this you need to use the Azapi provider since it’s not available with the Azurerm provider.
resource "azapi_resource" "DfSMDVMSettings" {
type = "Microsoft.Security/serverVulnerabilityAssessmentsSettings@2022-01-01-preview"
name = "AzureServersSetting"
parent_id = data.azurerm_subscription.current.id
body = jsonencode({
properties = {
selectedProvider = "MdeTvm"
}
kind = "AzureServersSetting"
})
schema_validation_enabled = false
}
I hope this blog post can help you to configure Defender for Cloud for your AVD subscription. The code can also be found on my Github here.
In case you have any questions, feel free to contact me on my socials or leave a comment.
1 thought on “Configure Defender for Cloud for an Azure Virtual Desktop subscription with Terraform”