Hi All,
You may have heard that Microsoft has announced that the default outbound internet access that Azure virtual machines, will end on 30 September 2025. The news can be read here.
What does this mean for the IT admin?
Until that date, your Azure virtual machines will be able to reach the internet by default. After that date, the IT admin will have to use other methods to make sure that outbound internet access is possible.
One of the most used methods to allow outbound internet access is using an Azure Firewall. In part 1 I showed how to deploy an Azure Firewall. In this part I show how to configure the firewall for the necessary AVD networking rules using IP Groups.
Rule collection group of classic rules?
When using an Azure firewall, the IT admin can configure the networking rules in 2 different ways. There are the classic firewall rules or the firewall policies. The below image shows the main differences between them both.
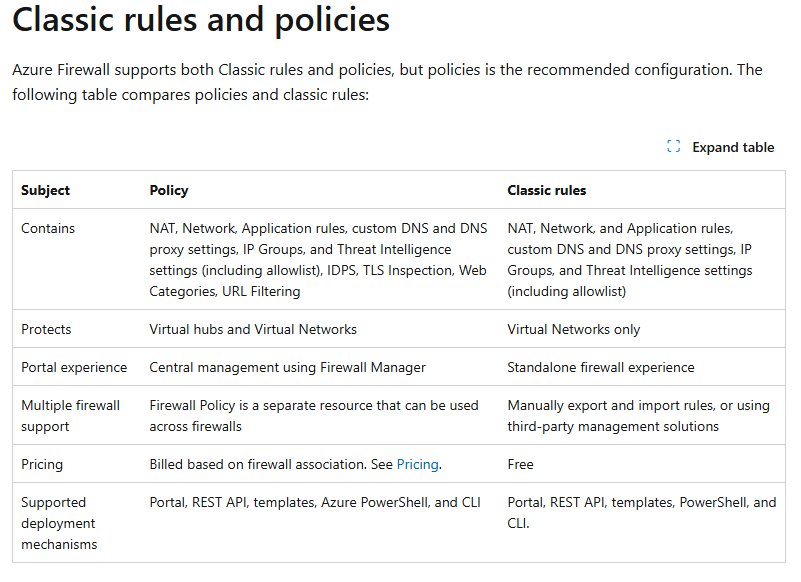
In this blog post I’ll show how to configure the classic rules. The classic rules can be found in the Azure Firewall menu.
To know which rules you need to configure for the AVD traffic, check out the following link.
The first thing to to is to create an data block for the Azure Firewall and the IP Group since these resources were created in part 1.
data "azurerm_firewall" "fw"{
name = "fw-hub-jvn-01"
resource_group_name = "rg-hub-${var.prefix}-networking-01"
}
data "azurerm_ip_group" "ipgroup-avd"{
name = "ipg-prd-jvn-avd-01"
resource_group_name = "rg-hub-${var.prefix}-networking-01"
}
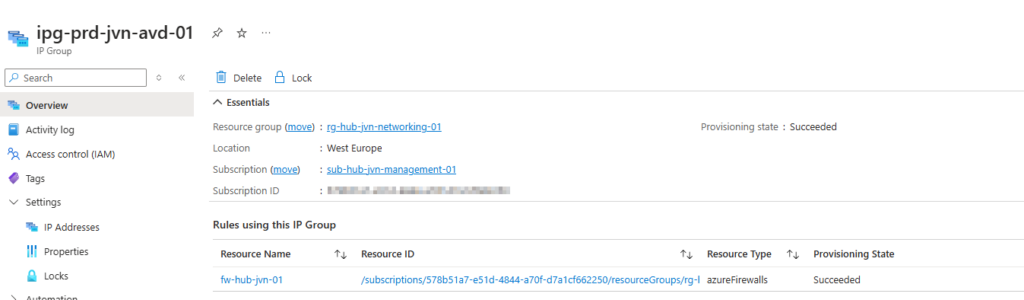
Now that we have all the required resources in place, it’s time to have a look at creating the necessary rules for the core AVD traffic.
resource "azurerm_firewall_network_rule_collection" "core-avd-rules-01" {
name = "core-avd-rules-01"
azure_firewall_name = data.azurerm_firewall.fw.name
resource_group_name = data.azurerm_resource_group.rg-fw.name
priority = 100
action = "Allow"
rule {
name = "WindowsVirtualDesktop"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"443",
]
destination_fqdns = [
"WindowsVirtualDesktop"
]
protocols = [
"TCP"
]
}
rule {
name = "AzureMonitor"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"443",
]
destination_fqdns = [
"AzureMonitor"
]
protocols = [
"TCP"
]
}
rule {
name = "AzureCloud"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"443",
]
destination_fqdns = [
"AzureCloud"
]
protocols = [
"TCP"
]
}
rule {
name = "Internet"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"1688",
]
destination_fqdns = [
"Internet"
]
protocols = [
"TCP"
]
}
rule {
name = "AzureFrontDoor.Frontend"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"443",
]
destination_fqdns = [
"AzureFrontDoor.Frontend"
]
protocols = [
"TCP"
]
}
rule {
name = "169.254.169.254"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"80",
]
destination_addresses = [
"169.254.169.254"
]
protocols = [
"TCP"
]
}
rule {
name = "168.63.129.16"
source_ip_groups = [
"/subscriptions/578b51a7-e51d-4844-a70f-d7a1cf662250/resourceGroups/rg-hub-jvn-networking-01/providers/Microsoft.Network/ipGroups/ipg-prd-jvn-avd-01"
]
destination_ports = [
"80",
]
destination_addresses = [
"168.63.129.16"
]
protocols = [
"TCP"
]
}
}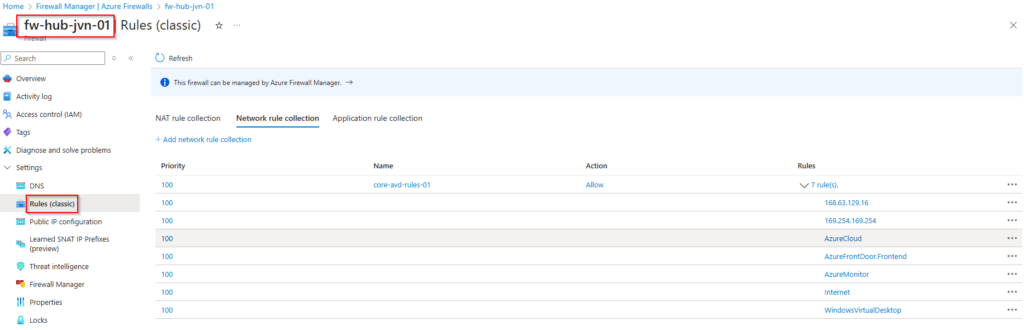
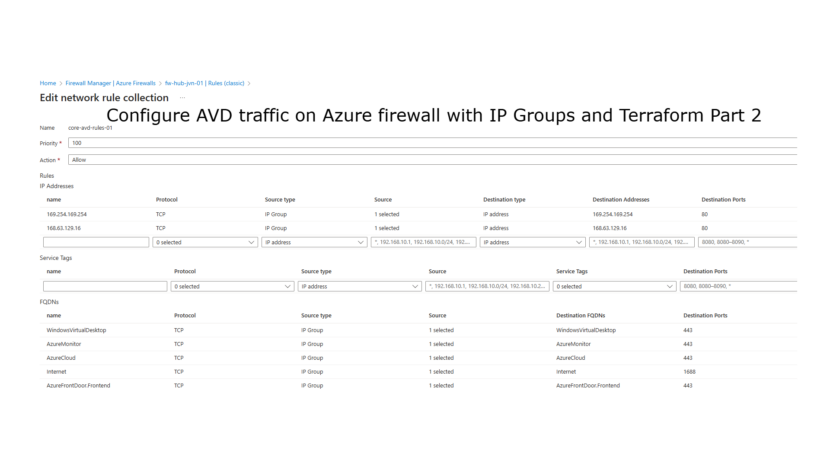
When we open the rules we can see that the IP Group is being used as the source. With this IP Group we can create more structure in the firewall rules and elimate the need to create firewall rules for each separate AVD subnet.
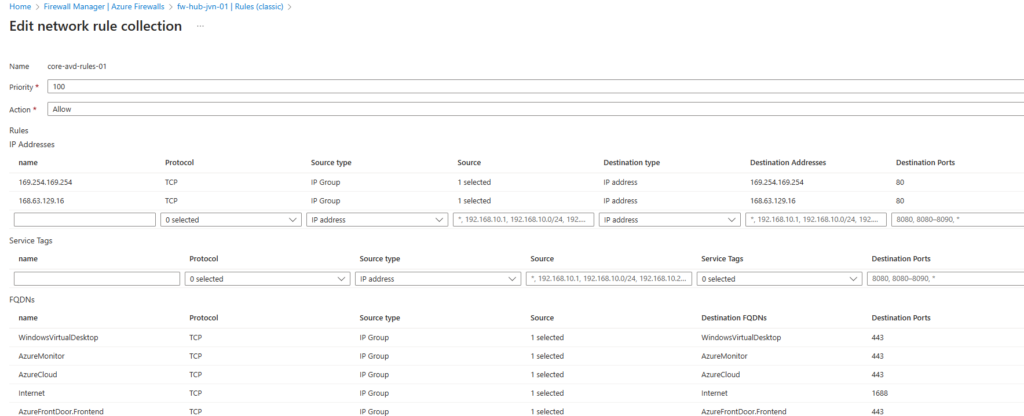
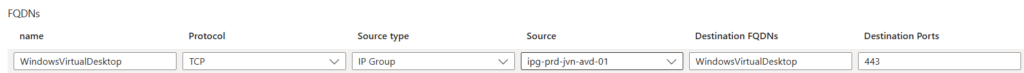
There you go, it’s very easy to create rules on Azure Firewall to allow the necessary traffic for the AVD hosts.
I hope you find this blogpost useful and that it can help you to configure the AVD traffic. Stay tuned for the next blogpost in this series about the default outbound traffic for AVD session hosts.
See you in part 3 of this mini series.