Data protection is very important whether you are working on-premise or in Azure. In this blog I’ll show you to deploy both of them using Terraform.
In Azure you have 2 options that you can use. An Recovery Services Vault or a Backup Vault. Both of these vault are different in what they can backup.
The Terraform script I use does all the following:
- Import the existing Log Analytics Workspace
- Create Resource Groups for recovery service vault
- Create Instant Restore Point Resource Group
- Create Recovery Services Vault and Backup Vault
- Enable all diagnostic settings for a backup
To see what the differences are go to Backup Center and click on +Vault
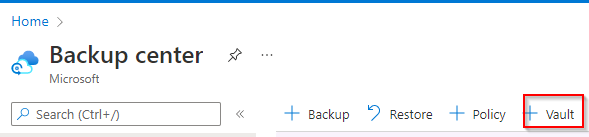
The next screen will appear to ask you what kind of vault you want to create.
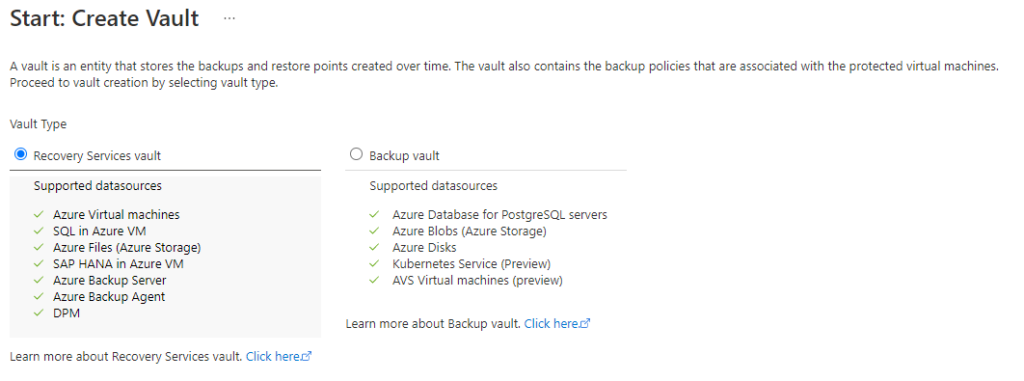
Recovery Services Vault
The first option that you have is the Recovery Services Vault. You can use this vault for both backup of resources but also for ASR. In this blog I’ll focus on the normal backup.
Import the existing Log Analytics Workspace
data "azurerm_log_analytics_workspace" "law" {
name = "law-hub-jvn-01"
resource_group_name = "rg-hub-jvn-law-01"
}Create resource groups
We need 2 resource groups. One resource group for the 2 vaults and one for the instant restore points. The reason why I create one for IRP is that otherwise it doesn’t follow your naming convention.
resource "azurerm_resource_group" "rsv-rg-prod" {
name = "rg-prod-${var.prefix}-backup-01"
location = var.location
tags = {
"Costcenter" = "IT"
"Location" = "Weu"
"Critical" = "Yes"
"Environment" = "Production"
"Solution" = "Backup"
}
}
resource "azurerm_resource_group" "rsv-rg-prod-irp" {
name = "rg-prod-${var.prefix}-backup-irp-01"
location = var.location
tags = {
"Costcenter" = "IT"
"Location" = "Weu"
"Critical" = "Yes"
"Environment" = "Production"
"Solution" = "Backup-irp"
}
}
Create Recovery Services Vault and Backup Vault
The below code is to create both vaults for production workloads.
resource "azurerm_recovery_services_vault" "rsv-prod" {
name = "rsv-prod-${var.prefix}-01"
location = azurerm_resource_group.rsv-rg-prod.location
resource_group_name = azurerm_resource_group.rsv-rg-prod.name
sku = "Standard"
soft_delete_enabled = true
tags = {
"Costcenter" = "IT"
"Location" = "Weu"
"Critical" = "Yes"
"Environment" = "Production"
"Solution" = "Backup"
}
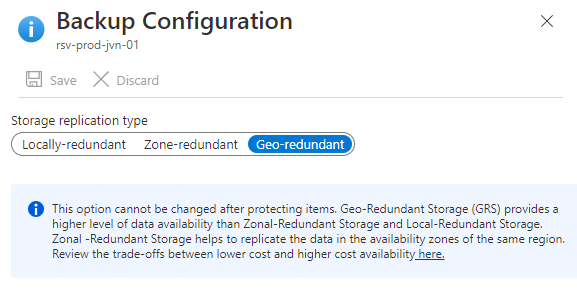
}With Terraform there is currently no option to change the “Storage Replication Type”. To change this you can use the following Powershell command. Remember that this can’t be changed if you already used the vault. The default setting is Geo-Redundant.
Set-AzRecoveryServicesBackupProperty -Vault $Vault01 -BackupStorageRedundancy ZoneRedundant
resource "azurerm_data_protection_backup_vault" "backup-vault" {
name = "vault-prod-${var.prefix}-01"
resource_group_name = azurerm_resource_group.rsv-rg-prod.name
location = azurerm_resource_group.rsv-rg-prod.location
datastore_type = "VaultStore"
redundancy = "LocallyRedundant" #changing this value will create a new vault / GeoRedundant
tags = {
"Costcenter" = "IT"
"Location" = "Weu"
"Critical" = "Yes"
"Environment" = "Production"
"Solution" = "Backup"
}
}The redundancy of the Backup Vault can’t be changed after you created it.
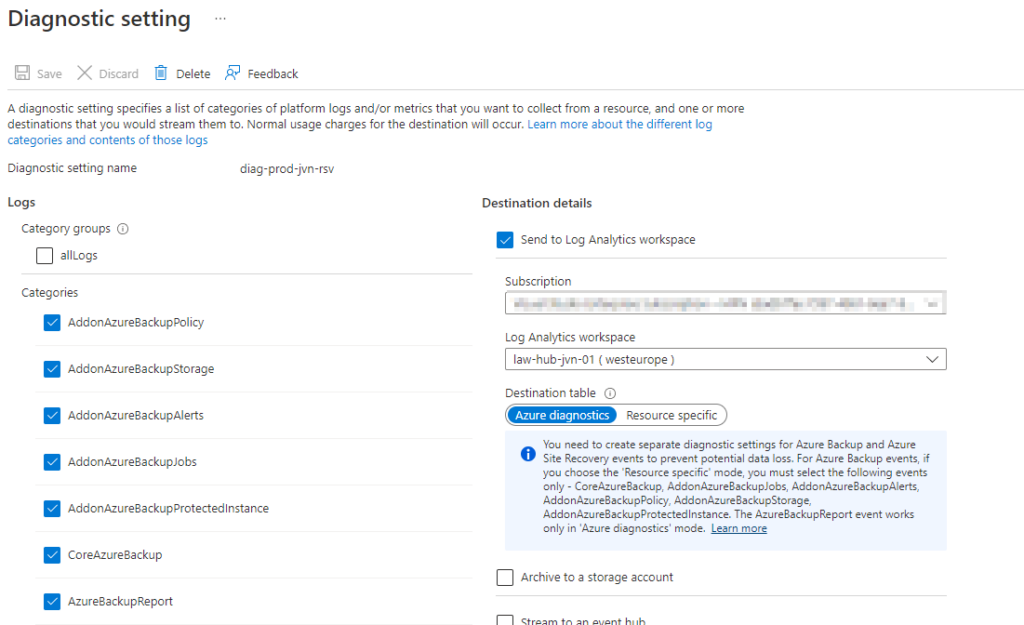
Enable all diagnostic settings for a backup
One the Recovery Services Vault there is the option to enable the diagnostic settings. In this case I only activate the settings for backup since I’m only gonna use this vault for backups and not for ASR.
resource "azurerm_monitor_diagnostic_setting" "rsv-prod-diag" {
name = "diag-prod-${var.prefix}-rsv"
target_resource_id = azurerm_recovery_services_vault.rsv-prod.id
log_analytics_workspace_id = data.azurerm_log_analytics_workspace.law.id
log {
category = "AzureBackupReport"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "CoreAzureBackup"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "AddonAzureBackupJobs"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "AddonAzureBackupAlerts"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "AddonAzureBackupPolicy"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "AddonAzureBackupStorage"
enabled = true
retention_policy {
enabled = true
}
}
log {
category = "AddonAzureBackupProtectedInstance"
enabled = true
retention_policy {
enabled = true
}
}
metric {
category = "AllMetrics"
retention_policy {
enabled = true
}
}
}
Now that you have the vaults it’s time to do some backups. You can view the entire code on my Github. I hope this script can be useful for you. If you have any questions feel free to reach out.
